Is NIS2 already stressing you out?
Per October 2024, all companies considered “critical” (energy, transport, digital infrastructure, manufacturing, to name a few) and all companies that are part of the supply chain of one of those companies must comply with NIS2. As well as all companies considered medium to large (i.e., any company with more than 250 FTE). That is quite a lot.
The fine for not complying: up to 10 million euro or 2% of global revenue (whichever one is higher). And (if that is not enough): the responsible managers are being held accountable as a natural person, meaning your board of directors could be sent to jail.
We did a quick count. Even though at Itility we serve a small number of customers (since we care for long-term, close partnerships) we will have at least 18 customers in scope for NIS2 compliance.
And since we are part of their supply chain, we are in scope, too.
Time for action!
Fortunately, we have been doing security projects for quite some time now and have done many assessments (IEC 62443, ISO27001, NIST, CRA, C2M2 or our own version). So, would this be ‘just’ a matter of combining all that knowledge into one overall approach?
Our view: yes. And after a deep dive into the topic with our security experts, we came up with not one, but with two approaches.
Approach 1
A quick scan to define which steps to take to initial compliancy, including identifying quick wins for major gaps. The quick scan includes an online survey on the topics shown on the radar below.
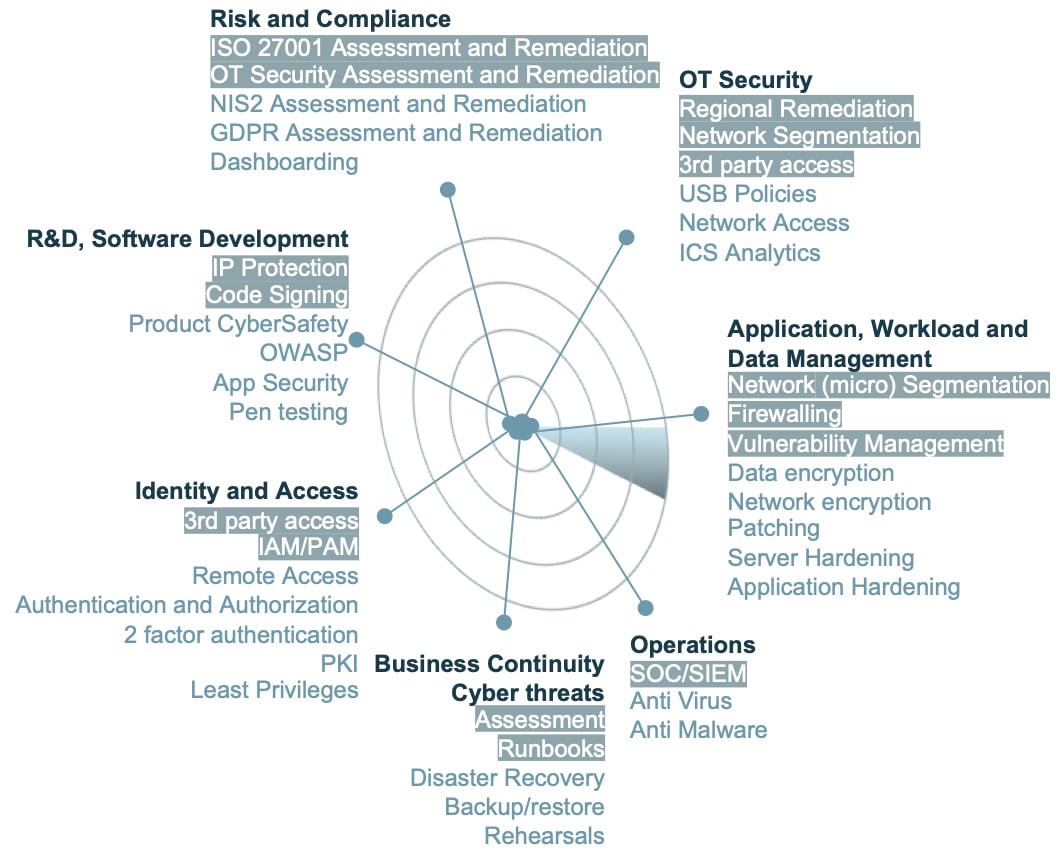
The survey is followed by compliancy determination via interviews with the risk categories. That is translated into an identification to define quick wins for gaps and ensure minimum compliancy.
Approach 2
This approach is a full framework. It starts with setting the baseline to assess the current compliancy level. This is to assess if you are affected, define gaps, and establish a detailed security posture.
With that, an accelerated implementation plan will be defined to meet management commitments and execute quick wins. The plan includes implementing security frameworks and policies for organizational and technical measures, which will be a tailored mix to the organization’s profile based on any of the following industry standards and frameworks: IEC 62443, ISO27001, CRA, C2M2, NIST. Having continuous monitoring in place can be a first step for your company, goal is to have processes and tooling in place for timely response and mitigation.
Time now to put the proof of the pudding in the eating
So in the coming months we will assess Itility, using approach 1 and then approach 2.
It might mean some investment… one of the articles below mentions that "22% budget increase is going to be needed for companies that haven’t done NIS2 before". However, another article mentions “with ISO 27001, you should be ok for NIS2”.
We are an efficient company and we do have ISO 27001 in place. We will keep you posted on how much budget we spent.
Here are some useful articles to get started on thinking NIS2:
NIS2 Directive explained: What’s coming and how to prepare with ISO 27001
Minimum Security Measures for Operators of Essentials Services